Any serious internet user (like yourself) should agree that mobile app usage and market share have touched new heights. According to eMarketer, smartphone users spend 88% of their time on mobile applications.

Mobile app developers have leveraged a situation of high mobile app usage, and so have attackers. Today, mobile application security is not just a feature or benefit, but an indispensable ingredient without which your app becomes futile. App developers, owners, and users are called upon to adopt mobile application security best practices if they want to stay on the safer side.
Failing to do so invites a host of threats and attacks whose repercussions are almost unbearable. It is universal knowledge that the cost of successful attacks has accelerated to extreme maximums. It is better to deal with mobile app attacks before they occur than after they do.
Top 7 Mobile App Security Checklist
It does not take much to secure your app. Here are some of the most budget-friendly mobile app security checklists and tips you can apply to secure your mobile app.
1. Use a Code Signing Certificate
Using a code signing certificate is one of the most fundamental security protocols you should consider for mobile app security. The certificate acts as a guarantee that the code of the mobile app is not corrupted or tampered with after being signed by the publisher. Apart from offering this assurance, the certificate also protects the app from malware infiltrations.
Developers who wish to ensure the utmost security for their mobile applications will have to purchase and install code signing certificates.
Usually, developers have two options – the extended validation certificate or the regular code signing certificate. Regular code signing certificates operate like typical OV (organization validation) SSL certificates. They are usually issued after a less-rigorous vetting process, meaning they are issued almost immediately. On the contrary, EV code signing certificates are only issued after extensive vetting of the publisher.
I highly recommend the EV code signing certificates because of the many security benefits they will bring to your mobile app. There are many authenticated SSL providers offer cheap code signing certificate or low-priced certs to increase software or app security.
2. Write a Secure Code
Attackers usually take advantage of the bugs and weaknesses in a code as grounds for initiating attacks. Most app intruders will attempt to reverse engineer the code to corrupt it. Previous research shows that malicious codes have been a nuisance, affecting over 11.6 million devices.
It is important to keep the security of your code in mind and ensure that the code remains secure at all times. For instance, it would be essential to harden the code through obfuscation and minification to protect it from reverse engineering attempts. Moreover, frequent code testing will help identify and mitigate bugs before they cause any serious harm to your mobile app. Last but not least, it is recommended to design a code that allows for easy updates that target vulnerable code areas.
3. Be Keen with Libraries
You must remain alert, especially when using third-party libraries. Although libraries are critical elements of your mobile app, they can, at times, provide residence to security threats. It was the same case with the GNU C Library, which portrayed a security flaw that allowed intruders to execute malicious codes from remote locations and crash systems. Surprisingly enough, this vulnerability was not discovered until after seven years. Imagine how much trouble the vulnerability had caused by then! For best mobile app security best practice, mobile app developers should use controlled internal repositories and enact code policies to safeguard their applications from vulnerabilities existing in the libraries.
4. Stick to Strong Authentication
Some of the most distressing security attacks that have happened in the past resulted from weak authentications. Personal identifiers that grant access to app accounts should remain as strong and unique as possible. Although end users hold significant power in the strength of the authentications, app developers also have a role to play by encouraging users to use only strong and unique authentication details.
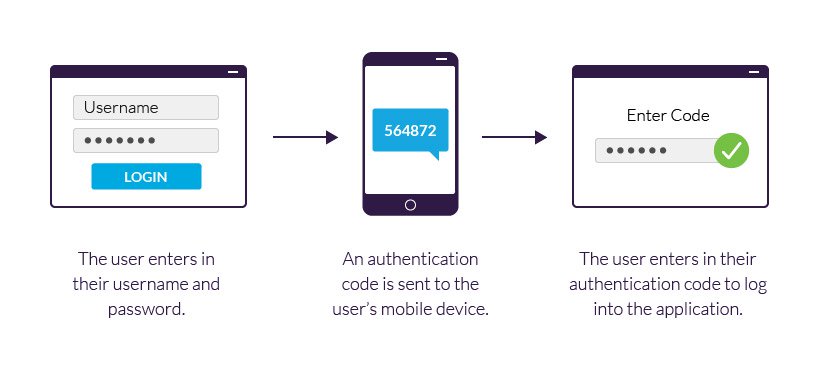
App developers should spell out the kind of usernames and passwords required for mobile applications. The app should be designed only to accept passwords of a given character length. The app should also allow users to change their passwords after a given specific period of time. But of great importance is to allow the users to use a two-step authentication factor when accessing their applications. Two-step authentication boosts the security of the app and protects it from unauthorized access. The app should thus accept two-step authentication factors such as the use of secret codes, one-time passwords, and biometric authentication.
5. The Principle of the Least Privilege
The principle of least privilege is a fundamental security concept that should apply to app security. According to the least privileged concept, a developer should allow codes to operate on only those permissions that the code absolutely needs to fulfill its key tasks, nothing more. The app should never request permissions or privileges more than the required maximum.
For instance, if the mobile app has no business with users’ contacts, there is no need to request them. Similarly, unnecessary network connections should not be allowed. The list goes on and on. So, always know what the app will need and that which the app does not need, and offer that which is absolutely necessary.
6. Regular App Testing and Updates
No platform is completely secure. There will always be dark spots that need to be handled. It is important that you access the dark spots before an enemy does. Regular app testing will help you discover vulnerable points and mitigate them before attackers take advantage of them. App security is a continuous process that only ends when you have no more business with the app. It would be great to invest in penetration and threat modeling to check your mobile app for vulnerabilities. It would also help if you kept every element of the app up to date. Updates usually come to address security vulnerabilities that existed in previous versions. Always ensure you use the update the moment they are released and tested.
7. Apply the Most Efficient Cryptography Techniques
If you want your encryption to yield the best results, you will have to pay more attention to key management. One of the best key cryptographic key practices is not to hardcore the keys, as that only makes them vulnerable to theft by malicious attackers. You should also ensure safe key storage and avoid local storage sources. Lastly, it would help to stick to the latest APIs, such as the 256-bit AES encryption.
Conclusion
Having a mobile app for your eCommerce store or business could be the right step to success. However, mobile applications also pose security challenges, which is why you must put in place adequate measures to ensure that the app is secure. This article explains some of the best guidelines to maintain mobile app security.




Leave a Comment